Phishing with malicious iso files
Phishing emails rely on many methods, such as sending exploit documents or executables. Thankfully, companies have figured out that this is common and implemented file attachment extension blockers, such as preventing external .pdf files and all .exe files.
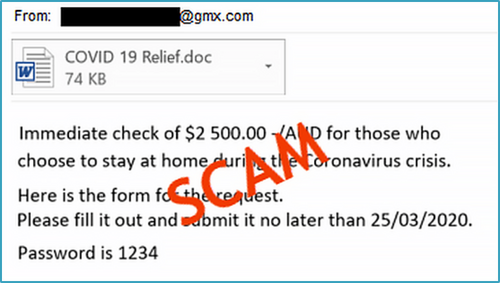
Above is an example from the ACSC.
Bypass
So how do you bypass this? Commonly you add a link or some javascript, but what if you just put your file inside of a container, such as zip or rar?
Phishing training does now cover this, but what about an iso?
cocaman reported one of these phishing emails on malware bazaar, with an Attachment.iso attachment.
From: "<<Canada Post Delivery>> canadapost@mailingconfirm.com" (likely spoofed)
Received: "from compassionate-mahavira.206-221-176-154.plesk.page (mail.mail-server-desk.com [206.221.176.154]) "
Date: "Fri, 25 Mar 2022 12:48:40 +0000"
Subject: "Delivery Updated"
Attachment: "Attachment.iso"
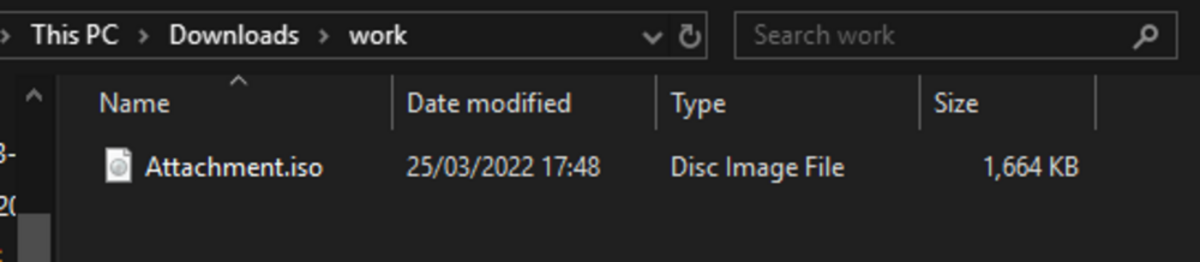
Windows makes it very easy to interact with .iso files, double clicking automatically makes it mount and show the disk image.
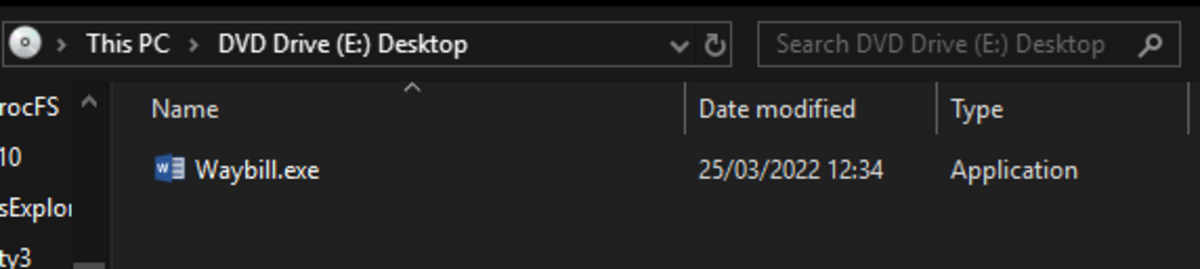
Hopefully the target at this point would notice that it is a .exe, but the classic word icon may fool them.
This specific sample leads to a DBatLoader dropping Remcos RAT. Triage has already created a config extractor for the remcos client and created a report.
This writeup hasn’t been technical, but it needs to be recognised that simple methods can bypass email safety rules, and users need to be trained for this rather than putting up minimal safety nets.