Face Brain: Password stealer with vm detection
![]()
Today I’m taking a look at a password stealer filled with obfuscation and some virtual machine detection. The sample can be obtained from malshare, with an automated analysis report on joesandbox.
| Property | Value |
|---|---|
| File Type | Portable Executable 64 |
| File Size | 3.69 MB |
| CompanyName | Say celebrate Date |
| FileDescription | Dress Suffer fuel basic |
| FileVersion | 6.4.14.15 |
| LegalCopyright | Pine Shit (c) 2005 |
| ProductName | Almost publication |
| MD5 | 3c7c6d236721ea4cef0f904ebde6f575 |
| SHA1 | d82cd631a49a175caace0fb209f7b9da16e29655 |
| SHA256 | ed107d31ac4a6e8f665986e3326cc2c4551fd00ba26f5414faa8edd0f7c20061 |
Initial overview
The sandbox report provides us with a lot of useful initial information. It tells us that it’s attempting to steal credentials, and contains anti-analysis techniques such as dummy data, code obfuscation and cpuid.
Junk data
There are several techniques used in this sample to evade analysis. For example, there’s a lot of dummy base64 strings to annoy me a bit.
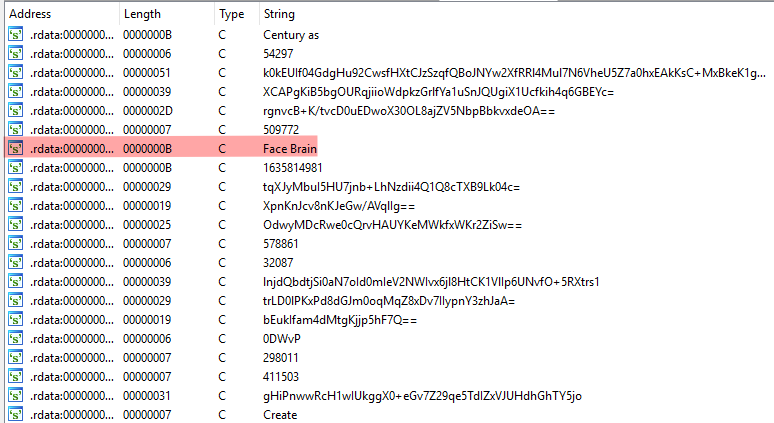
Among them is the string I used for naming this sample, since it doesn’t appear to have a classification.
There’s also a lot of general dummy strings.
Initial run
When I initially ran this, I observed a high CPU usage, probably from whatever it’s doing after loading some crypto libraries, followed by the process exiting. That’s not my expectation.
Work around
The sandbox signatures mentioned Contains functionality to query CPU information (cpuid).
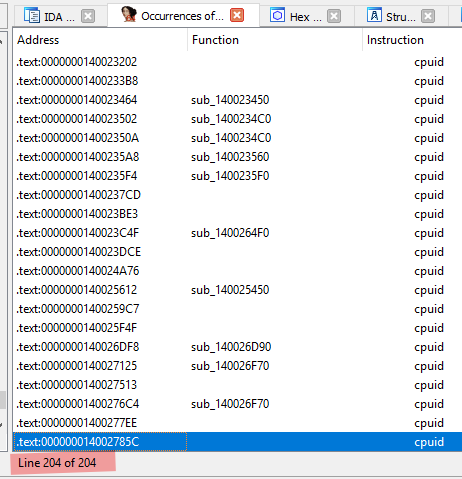
There’s 204 mentions of cpuid, because this sample is quite heavily obfuscated.
To defeat this anti-vm technique, there’s a great post on Sina & Shahria’s Blog about it.
I don’t know which registers are being used for this detection, so I’ll write over them all:
cpuid.1.rax="0---:----:----:----:----:----:----:----:----:----:----:----:----:----:----:----"
cpuid.1.rbx="0---:----:----:----:----:----:----:----:----:----:----:----:----:----:----:----"
cpuid.1.rcx="0---:----:----:----:----:----:----:----:----:----:----:----:----:----:----:----"
cpuid.1.rdx="0---:----:----:----:----:----:----:----:----:----:----:----:----:----:----:----"
cpuid.1.rex="0---:----:----:----:----:----:----:----:----:----:----:----:----:----:----:----"
cpuid.1.r8="0---:----:----:----:----:----:----:----:----:----:----:----:----:----:----:----"
cpuid.1.r9="0---:----:----:----:----:----:----:----:----:----:----:----:----:----:----:----"
cpuid.1.r10="0---:----:----:----:----:----:----:----:----:----:----:----:----:----:----:----"
cpuid.1.r11="0---:----:----:----:----:----:----:----:----:----:----:----:----:----:----:----"
cpuid.1.r12="0---:----:----:----:----:----:----:----:----:----:----:----:----:----:----:----"
cpuid.1.r13="0---:----:----:----:----:----:----:----:----:----:----:----:----:----:----:----"
cpuid.1.r14="0---:----:----:----:----:----:----:----:----:----:----:----:----:----:----:----"
cpuid.1.r15="0---:----:----:----:----:----:----:----:----:----:----:----:----:----:----:----"
cpuid.1.r16="0---:----:----:----:----:----:----:----:----:----:----:----:----:----:----:----"
I append this to my vmware virtual machine’s .vmx file.
Continued run
Now that the anti-vm detection has been defeated, I can focus on the stealing part itself.
The code is heavily obfuscated, complete spaghetti, so I’m not going to bother with a lot of static analysis, simply what’s going on in procmon.
Data collected
| Data | Evidence |
|---|---|
| Computer Name | 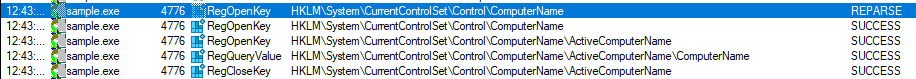 |
| WinSCP sessions |  |
| FileZilla credentials | 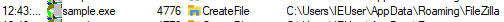 |
| Firefox credentials | 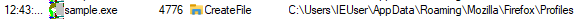 |
| Microsoft Edge credentials |  |
| Yandex browser credentials |  |
| Brave browser credentials | 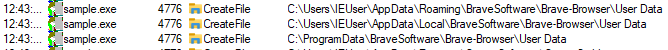 |
| Opera credentials |  |
| Google Chrome credentials | 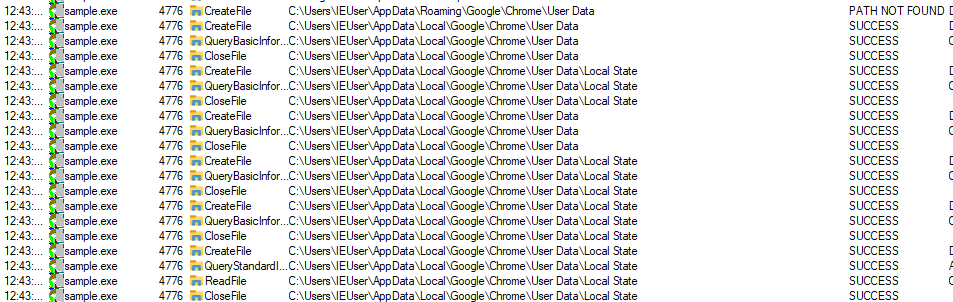 |
| 7 Star browser credentials |  |
| Amigo browser credentials |  |
| Cent browser credentials |  |
| Chedot browser credentials | 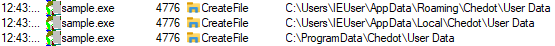 |
| Google chrome SxS credentials | 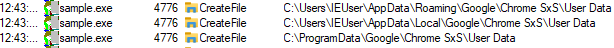 |
| Chromium credentials |  |
| CocCoc browser credentials | 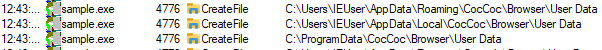 |
| Comodo browser credentials |  |
| Elements browser credentials | 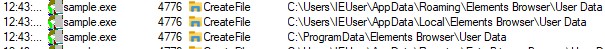 |
| Epic Privacy browser credentials |  |
| Kometa browser credentials |  |
| Orbitum browser credentials | 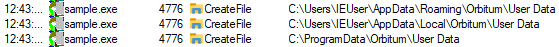 |
| Sputnik browser credentials | 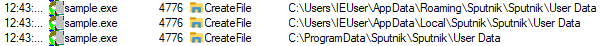 |
| Torch browser credentials | 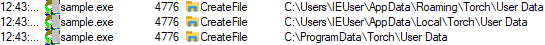 |
| Ucoz Media Uran browser credentials | 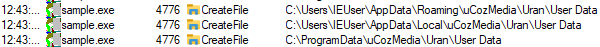 |
| Vivaldi browser credentials | 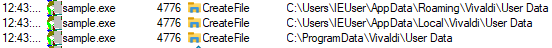 |
Calling home
Once all the credentials are collected, it sends it back to a server from a Lithuanian hosting provider that is a known spam hoster.
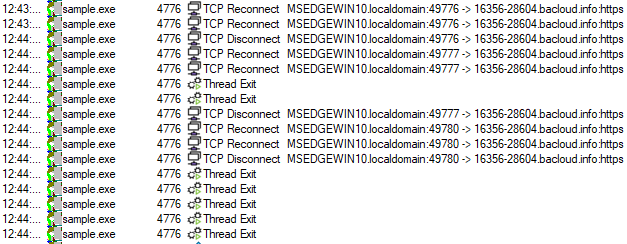
Conclusion
This is a fairly comphrensive stealer in terms of browsers, and it’s certainly very well obfuscated. However, it doesn’t detect its environment well. The anti-vm can be easily defeated, and it doesn’t even check for debuggers, nor analysis tools such as procmon.